In the realm of security, the importance of an efficient IP Access Controller cannot be overstated. According to security expert Dr. Emily Carter, "The right IP Access Controller can transform security measures from reactive to proactive." This transformation is essential as organizations face increasing threats in today's digital landscape.
Selecting the best IP Access Controller for 2026 is crucial. Many solutions promise enhanced security performance, yet not all deliver. The market is flooded with options. Organizations need to assess their specific needs carefully. A suitable controller should provide scalability, ease of use, and robust integration capabilities. It's vital to examine user experiences and product reviews for assurance.
Security technologies must evolve, yet imperfections remain. Some controllers may lack essential features or present complex interfaces. Users often overlook these flaws during the selection process, leading to potential vulnerabilities. It's not just about choosing the latest model; it's about finding a reliable partner in security. Ultimately, an informed choice will lead to a safer, more secure environment for all users.

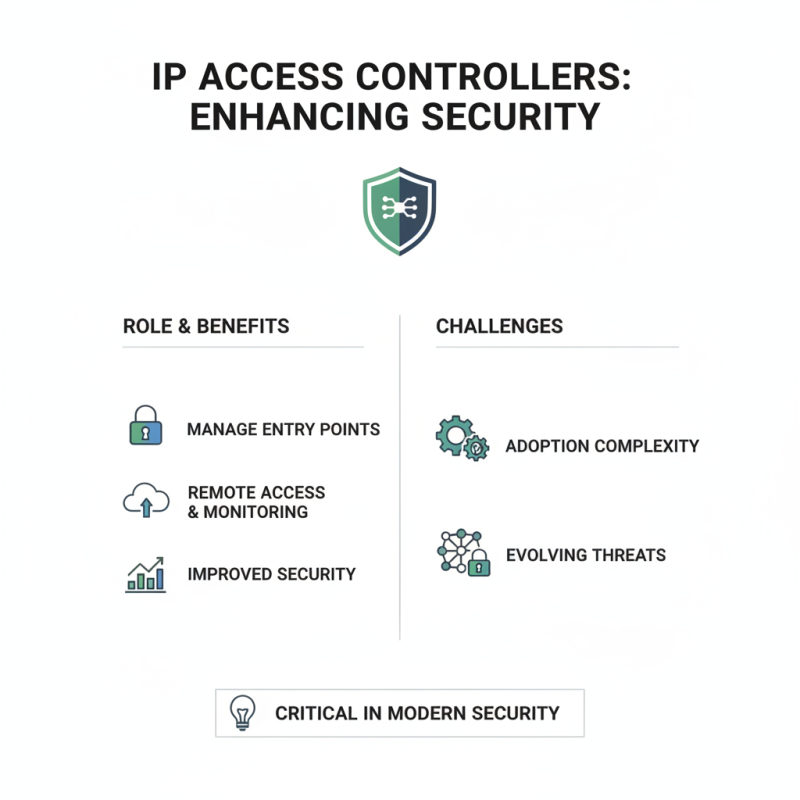
In an era where security threats are constantly evolving, IP access controllers play a critical role. These devices manage entry points in a facility. They offer remote access control and monitoring. This helps enhance security performance significantly. However, there are challenges in adopting these technologies.
Many organizations still rely on outdated systems. This can create vulnerabilities. IP access controllers can bring multiple benefits, such as real-time alerts and customizable access levels. Yet, implementing them requires careful planning. Not every solution fits every environment. Potential users may face budgeting issues or a lack of skilled personnel.
Understanding the importance of these devices is essential. Information privacy is at stake. Access control is not just about locking doors. Improving security requires a comprehensive approach. IP access controllers must be part of a larger security strategy. This means regular updates and maintenance are necessary. Without these, the system may fail to protect effectively.
Choosing the right IP access controller is vital for improved security performance. These devices manage who enters a space, protecting assets and sensitive information. Key features should include real-time monitoring capabilities. This allows users to oversee access events as they occur. Many also offer integration with existing security systems, enhancing overall safety.
User-friendly interfaces are essential. A complex system can frustrate users, leading to errors. Additionally, advanced encryption methods should be standard. They safeguard data from unauthorized access. Some controllers even provide biometric options, like fingerprint scanning. This adds an extra layer of security.
Another important feature is remote access. Being able to control the system from anywhere improves convenience. However, this convenience can create vulnerabilities. Regular updates are necessary to address potential security flaws. Finally, a reliable support network is crucial. Users must feel confident they can resolve issues quickly. In this field, even minor oversights can lead to serious consequences.
The demand for IP access controllers is rising sharply. Recent industry reports indicate that the market is projected to grow by 15% annually. Enhanced security measures drive this growth. Many businesses are investing significantly in technology to protect sensitive data and infrastructure.
In 2026, various brands claim to offer top-tier performance. A comparative analysis reveals key features that stand out. For instance, advanced authentication methods like biometric scanning are becoming essential. Additionally, seamless integration with existing security systems is a priority for many organizations. Not every product delivers on these promises, leading to confusion among buyers.
User feedback often highlights mixed experiences. Some devices work flawlessly, while others pose challenges with installation and setup. Security breaches continue to occur, prompting companies to rethink their strategies. The balance between cost and efficiency remains a critical concern. Data shows that companies investing in higher-quality controllers report fewer incidents. However, many still rely on outdated systems, risking their overall security posture. The market is evolving, but customers must remain vigilant in their choices.
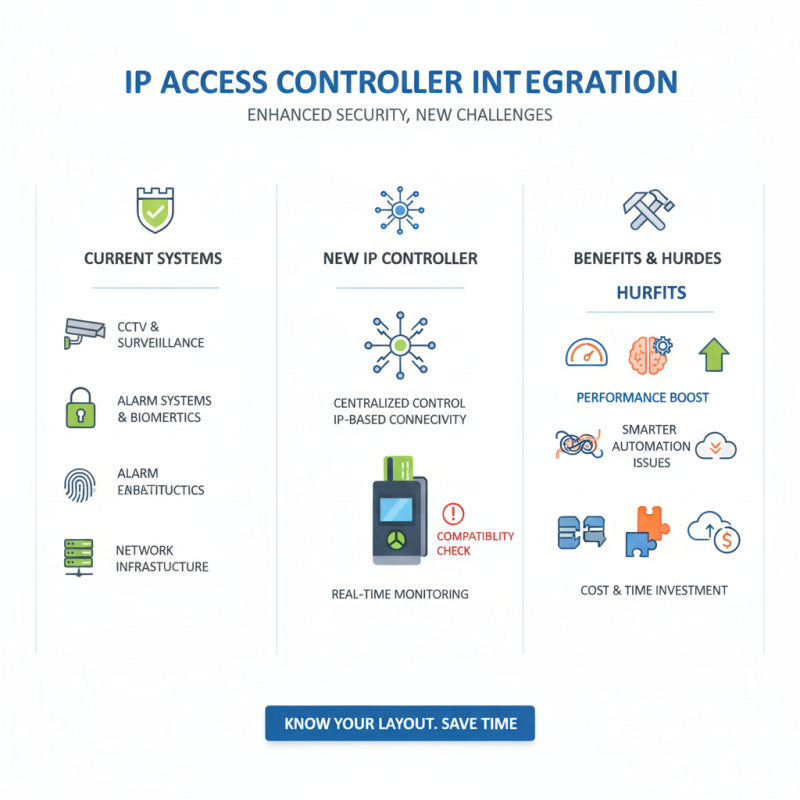
Integrating an IP access controller with existing security systems can significantly enhance performance. However, it comes with challenges. Understanding the current layout is key. Assess what systems are already in place. Ensure compatibility with your new access controller. This will save time and avoid frustration.
One effective tip is to conduct a comprehensive audit of your current systems. Inspect how they function individually and together. Identify weaknesses. This will guide your integration process. Often, organizations overlook small discrepancies, leading to security gaps.
Another useful approach is to involve all stakeholders. Everyone should understand the benefits of the new system. Communication can help ease the transition. Training is also essential. Users must know how to interact with the new technology. It's critical for smooth operations. Remember, embracing new tech isn’t just about installation. It's about adaptation and ongoing improvement.
The future of IP access control technology is evolving rapidly. Enhanced security performance is a key focus. Advanced algorithms will analyze patterns. This can help identify suspicious activities in real-time. It's crucial for businesses that prioritize safety. Yet, technology must be adaptable. As threats evolve, so must our responses.
Integration is a major trend. Systems will connect seamlessly with other security tools. This creates a unified defense strategy. However, relying on technology alone can be risky. Human oversight is still necessary. If tech fails, what are the backup plans? Organizations need to evaluate their dependence on automated systems.
User experience is also important. Simple interfaces can improve effectiveness. But, will this compromise security for convenience? Finding the right balance is challenging. Organizations must continually refine their systems. This requires ongoing reflection and adaptation. The landscape of security technology is complex and ever-changing. Adjustments will always be needed to stay protected.